Cyber Security for Small Business
Data Security - A Strategic Imperative for CPA ...
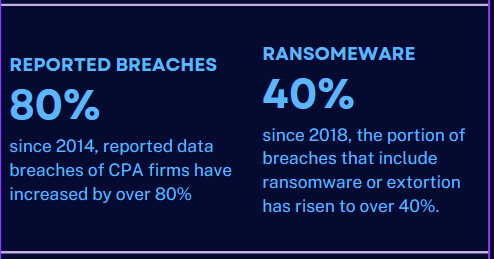
Data security is an increasingly important topic for CPA firms, as the number of attacks and the associated costs of these attacks continue to grow. Cyber criminals are targeting CPA...
Data Security - A Strategic Imperative for CPA ...
Data security is an increasingly important topic for CPA firms, as the number of attacks and the associated costs of these attacks continue to grow. Cyber criminals are targeting CPA...

Effective Practices for 3rd Party Vendor Manage...
What is Third Party Vendor Management? Third Party Vendor Management in Cyber Security is the process of managing external vendors who provide services and products that are related to IT...
Effective Practices for 3rd Party Vendor Manage...
What is Third Party Vendor Management? Third Party Vendor Management in Cyber Security is the process of managing external vendors who provide services and products that are related to IT...

Assigning Low/Medium/High Risk Severity to PII/...
The following describe the three impact levels—low, moderate, and high—defined in FIPS 199, which are based on the potential impact of a security breach involving a particular system: LOW - if...
Assigning Low/Medium/High Risk Severity to PII/...
The following describe the three impact levels—low, moderate, and high—defined in FIPS 199, which are based on the potential impact of a security breach involving a particular system: LOW - if...

4 Steps to Minimize Risk Associated with PII an...
Minimizing the use, collection, and retention of PII (Personally Identifiable Information) involves limiting the amount of data collected and stored, as well as using data security measures to protect and...
4 Steps to Minimize Risk Associated with PII an...
Minimizing the use, collection, and retention of PII (Personally Identifiable Information) involves limiting the amount of data collected and stored, as well as using data security measures to protect and...

Identifying Personal Identifiable Information (...
What is PII ? PII stands for Personally Identifiable Information, and refers to any data that can be used to identify a specific person. This includes things like full name,...
Identifying Personal Identifiable Information (...
What is PII ? PII stands for Personally Identifiable Information, and refers to any data that can be used to identify a specific person. This includes things like full name,...

Cybersecurity Regulations for Law firms and Acc...
What are Cybersecurity Regulations? Why are Cybersecurity Regulations Important for Small Law Firms and Accounting Firms? Identifying Different Types of Cybersecurity Regulations Establish A security Program What are Cybersecurity Regulations...
Cybersecurity Regulations for Law firms and Acc...
What are Cybersecurity Regulations? Why are Cybersecurity Regulations Important for Small Law Firms and Accounting Firms? Identifying Different Types of Cybersecurity Regulations Establish A security Program What are Cybersecurity Regulations...
